Integrate DefectDojo
Inspect the main steps to perform for installing DefectDojo via Helm Chart.
It is also possible to install DefectDojo using the add-ons approach. For details, please refer to the KubeRocketCI addons approach.
Prerequisites
- Kubectl version 1.26.0+ is installed. Please refer to the Kubernetes official website for details.
- Helm version 3.14.0+ is installed. Please refer to the Helm page on GitHub for details.
Installation
Please refer to the DefectDojo Helm Chart and Deploy DefectDojo into the Kubernetes cluster sections for details.
To install DefectDojo, follow the steps below:
-
Check that a security namespace is created. If not, run the following command to create it:
kubectl create namespace defectdojoFor the OpenShift usersWhen using the OpenShift platform, install the
SecurityContextConstraintsresource. In case of using a custom namespace fordefectdojo, change the namespace in theuserssection.View: defectdojo-scc.yaml
allowHostDirVolumePlugin: false
allowHostIPC: false
allowHostNetwork: false
allowHostPID: false
allowHostPorts: false
allowPrivilegeEscalation: true
allowPrivilegedContainer: false
allowedCapabilities: null
apiVersion: security.openshift.io/v1
allowedFlexVolumes: []
defaultAddCapabilities: []
fsGroup:
type: MustRunAs
ranges:
- min: 999
max: 65543
groups: []
kind: SecurityContextConstraints
metadata:
annotations:
"helm.sh/hook": "pre-install"
name: defectdojo
priority: 1
readOnlyRootFilesystem: false
requiredDropCapabilities:
- KILL
- MKNOD
- SETUID
- SETGID
runAsUser:
type: MustRunAsRange
uidRangeMin: 1
uidRangeMax: 65543
seLinuxContext:
type: MustRunAs
supplementalGroups:
type: RunAsAny
users:
- system:serviceaccount:defectdojo:defectdojo
- system:serviceaccount:defectdojo:defectdojo-rabbitmq
- system:serviceaccount:defectdojo:default
volumes:
- configMap
- downwardAPI
- emptyDir
- persistentVolumeClaim
- projected
- secret -
Add a chart repository:
helm repo add defectdojo 'https://raw.githubusercontent.com/DefectDojo/django-DefectDojo/helm-charts'
helm repo update -
Create PostgreSQL admin secret:
kubectl -n defectdojo create secret generic defectdojo-postgresql-specific \
--from-literal=postgresql-password=<postgresql_password> \
--from-literal=postgresql-postgres-password=<postgresql_postgres_password>noteThe
postgresql_passwordandpostgresql_postgres_passwordpasswords must be 16 characters long. -
Create Rabbitmq admin secret:
kubectl -n defectdojo create secret generic defectdojo-rabbitmq-specific \
--from-literal=rabbitmq-password=<rabbitmq_password> \
--from-literal=rabbitmq-erlang-cookie=<rabbitmq_erlang_cookie>noteThe
rabbitmq_passwordpassword must be 10 characters long.The
rabbitmq_erlang_cookiepassword must be 32 characters long. -
Create DefectDojo admin secret:
kubectl -n defectdojo create secret generic defectdojo \
--from-literal=DD_ADMIN_PASSWORD=<dd_admin_password> \
--from-literal=DD_SECRET_KEY=<dd_secret_key> \
--from-literal=DD_CREDENTIAL_AES_256_KEY=<dd_credential_aes_256_key> \
--from-literal=METRICS_HTTP_AUTH_PASSWORD=<metric_http_auth_password>noteThe
dd_admin_passwordpassword must be 22 characters long.The
dd_secret_keypassword must be 128 characters long.The
dd_credential_aes_256_keypassword must be 128 characters long.The
metric_http_auth_passwordpassword must be 32 characters long. -
Install DefectDojo v.2.22.4 using defectdojo/defectdojo Helm chart v.1.6.69:
helm upgrade --install \
defectdojo \
--version 1.6.69 \
defectdojo/defectdojo \
--namespace defectdojo \
--values values.yamlCheck out the values.yaml file sample of the DefectDojo customization:
View: values.yaml
tag: 2.22.4
fullnameOverride: defectdojo
host: defectdojo.<ROOT_DOMAIN>
site_url: https://defectdojo.<ROOT_DOMAIN>
alternativeHosts:
- defectdojo-django.defectdojo
initializer:
# should be false after initial installation was performed
run: true
django:
ingress:
enabled: true # change to 'false' for OpenShift
activateTLS: false
uwsgi:
livenessProbe:
# Enable liveness checks on uwsgi container. Those values are use on nginx readiness checks as well.
# default value is 120, so in our case 20 is just fine
initialDelaySeconds: 20 -
For the OpenShift platform, install a Route:
View: defectdojo-route.yaml
kind: Route
apiVersion: route.openshift.io/v1
metadata:
name: defectdojo
namespace: defectdojo
spec:
host: defectdojo.<ROOT_DOMAIN>
path: /
tls:
insecureEdgeTerminationPolicy: Redirect
termination: edge
to:
kind: Service
name: defectdojo-django
port:
targetPort: http
wildcardPolicy: None
Configuration
To prepare DefectDojo for integration with KubeRocketCI, follow the steps below:
-
Create ci user in DefectDojo UI:
-
Login to DefectDojo UI using admin credentials:
echo "DefectDojo admin password: $(kubectl \
get secret defectdojo \
--namespace=defectdojo \
--output jsonpath='{.data.DD_ADMIN_PASSWORD}' \
| base64 --decode)" -
Go to User section
-
Create new user with write permission:
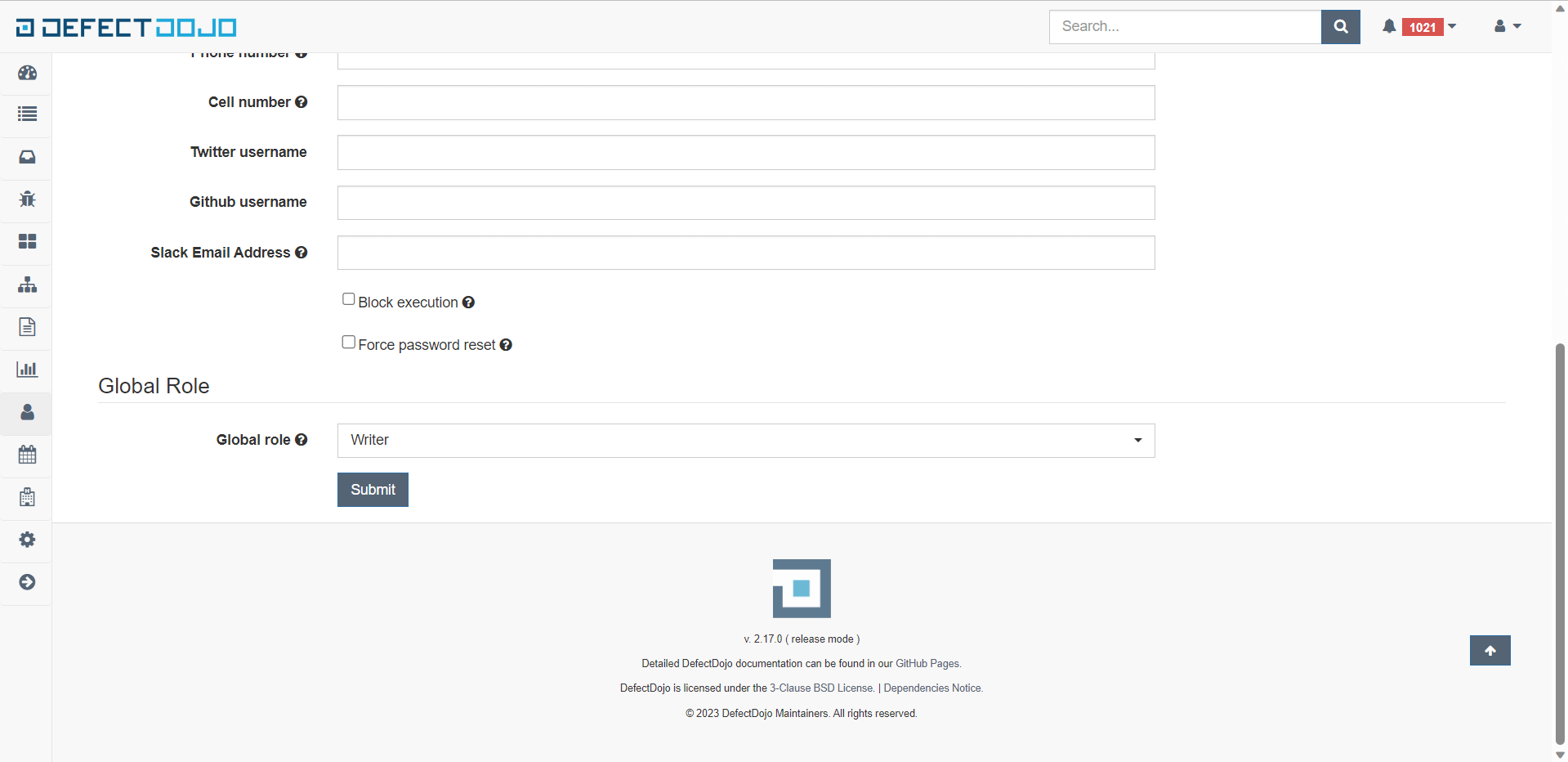
-
-
Get a token of the DefectDojo user:
-
Login to the DefectDojo UI using the credentials from previous steps.
-
Go to the API v2 key (token).
-
Copy the API key.
-
-
Provision the secret using
Portal UI,Manifestor with theexternalSecretsoperator:- UI Portal
- Manifest
- External Secrets Operator
Go to the Portal open Configuration -> SECURITY -> DEFECTDOJO. Update or click + ADD INTEGRATION fill fields
Quick Link URL,URLandTokenclick thesavebutton.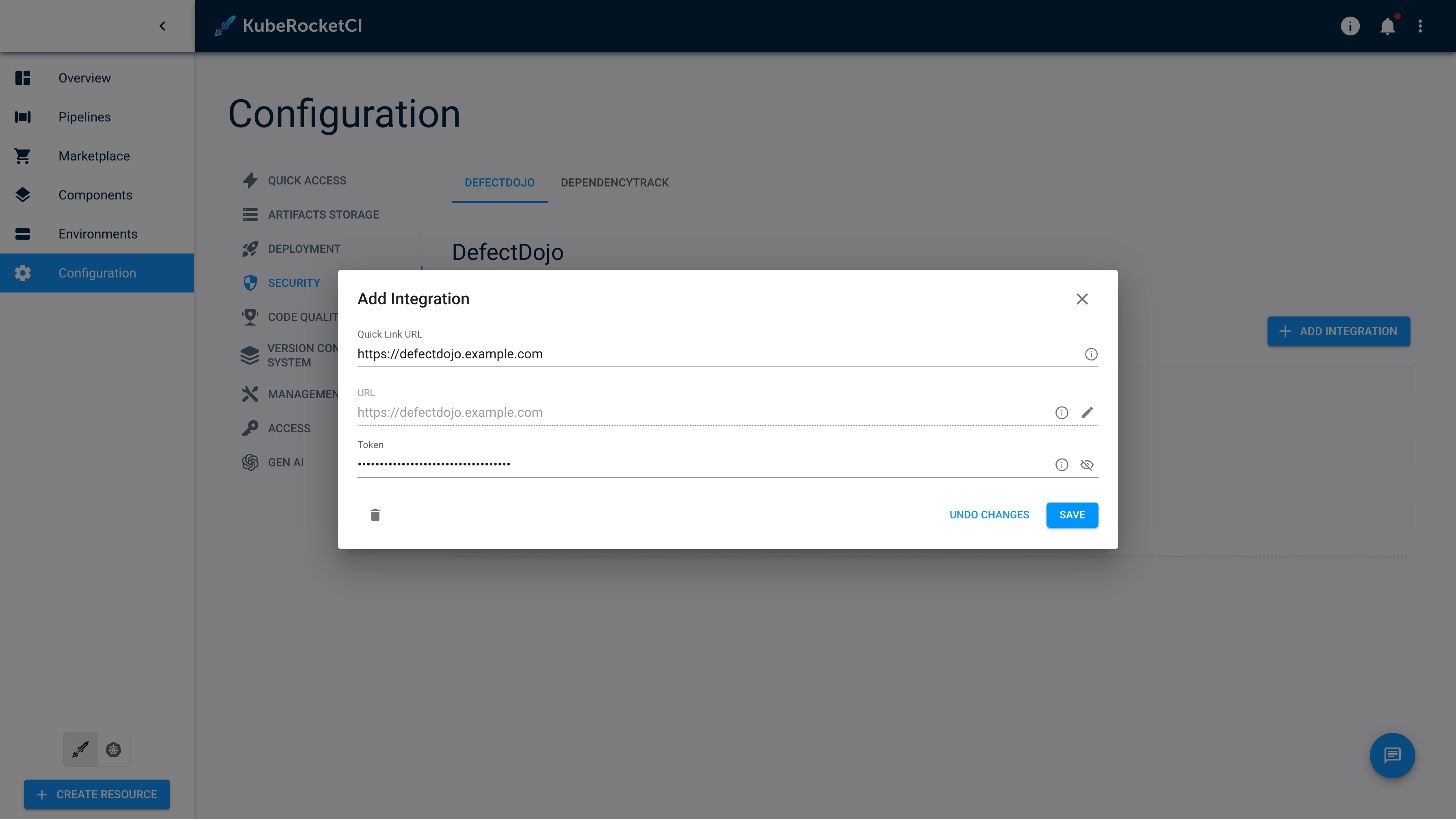
apiVersion: v1
kind: Secret
metadata:
name: ci-defectdojo
namespace: edp
labels:
app.edp.epam.com/secret-type: defectdojo
app.edp.epam.com/integration-secret: "true"
stringData:
url: https://defectdojo.example.com
token: <token>Store defectdojo URL and Token in AWS Parameter Store with following format:
"ci-defectdojo":
{
"url": "https://defectdojo.example.com",
"token": "XXXXXXXXXXXX"
}Go to the Portal open Configuration -> SECURITY -> DefectDojo and see the
Managed by External Secretmessage.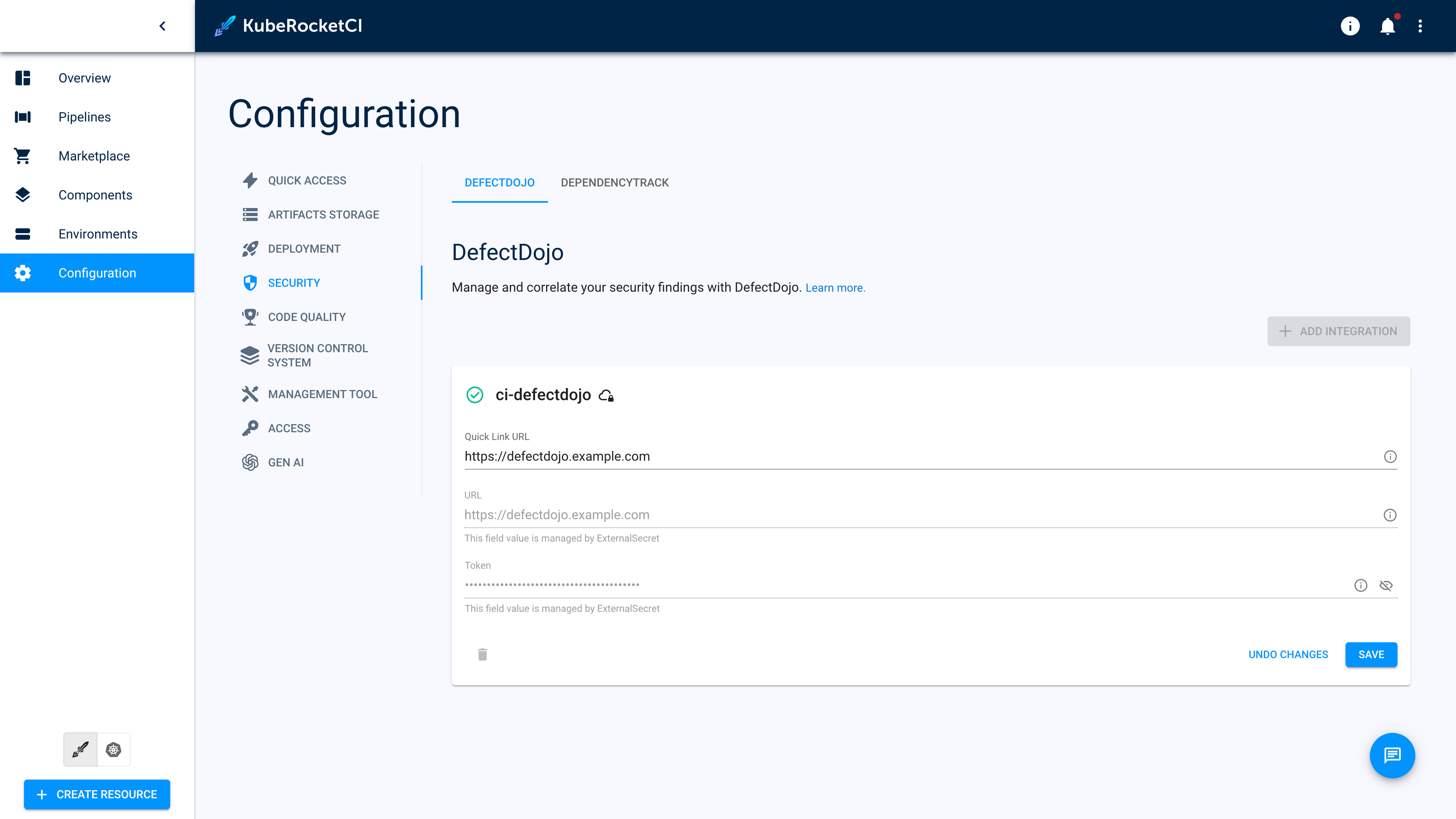
More details about the External Secrets Operator integration procedure can be found in the External Secrets Operator Integration page.
After following the instructions provided, you should be able to integrate your DefectDojo with the KubeRocketCI using one of the available scenarios.